Multiple Vulnerabilities in KaiOS Pre-installed Mobile Applications

I found multiple HTML injection vulnerabilities in several KaiOS mobile applications that are pre-installed on KaiOS mobile devices (this is just a repost of the original found on the NCC Group research page). While exploiting an HTML injection vulnerability in a Firefox OS, or KaiOS, the application normally has limited impact besides the ability to manipulate the application's user interface, I also used a CSP bypass in order to gain remote JavaScript injection, which allowed for abusing privileged JavaScript APIs (remotely stealing files from the device was possible).
The following vulnerabilities affected multiple KaiOS mobile devices:
The Email application is vulnerable to HTML and JavaScript injection attacks.
We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a remote attacker to inject in JavaScript that will execute in the context of the Email application, which has access to sensitive Web APIs, such as the storage, settings, and contacts Web APIs, which would allow a remote attacker to steal files stored on the SD card, such as the user's photos, videos, or audio, and alter device settings.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
The following video demonstrates that remote exploitation resulting in remote file disclosure is possible.
The Contacts application is vulnerable to HTML and JavaScript injection attacks.
It is also possible to bypass the default CSP used by certified applications, which allows a remote attacker to inject in JavaScript that will execute in the context of the Contacts application, which has access to sensitive Web APIs, such as the storage, settings, and contacts Web APIs, which would allow a remote attacker to steal files stored on the SD card, such as the user's photos, videos, or audio, and alter device settings.
The vulnerability could be exploited remotely if an attacker creates a vCard file using the first or last name that includes HTML content. The attacker then sends the vCard file as an email attachment to an email account that is set up on the mobile device. When the user selects the attachment from within the Email mobile application, then the Contacts application will open. If the user agrees to save the contact and then reopen the Contacts application then HTML injection will occur.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
The File Manager application is vulnerable to HTML and JavaScript injection attacks.
We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a remote attacker to inject in JavaScript that will execute in the context of the File Manager application, which has access to sensitive Web APIs, such as the storage Web APIs, which would allow a remote attacker to steal files stored on the SD card, such as the user's photos, videos, or audio. On mobile devices where the File Manager has been granted access to an undocumented engineering mode Web API, it is possible to execute arbitrary OS commands as the root user by exploiting this vulnerability.
The vulnerability can be exploited locally by connecting the mobile device to a computer using USB and transferring the malicious file to the mobile device's internal storage using MTP. Opening the File Manager application and viewing the malicious filename triggers HTML injection into the mobile application.
The vulnerability can be exploited remotely by sending the file as an email attachment to an email account that is set up on a mobile device. If the user downloads the file attachment and then accesses the downloads directory via the File Manager application.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
The Recorder application is vulnerable to HTML and JavaScript injection attacks.
It is also possible to bypass the default CSP used by certified applications, which allows a local attacker to inject in JavaScript that will execute in the context of the Recorder application, which has access to sensitive Web APIs, such as the storage and settings Web APIs, which would allow a local attacker to manipulate files stored on the SD card, such as the user's photos, videos, or audio, and alter device settings.
The vulnerability can be exploited locally by opening the Recorder application and creating a new audio recording with a name that contains HTML.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
The Note application is vulnerable to HTML and JavaScript injection attacks.
We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a local attacker to inject in JavaScript that will execute in the context of the Note application, which has access to sensitive Web APIs, such as the storage Web APIs, which would allow a local attacker to manipulate files stored on the SD card, such as the user's photos, videos, or audio.
The vulnerability can be exploited locally by opening the Note application and creating a new note with contents that contain HTML.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
The FM Radio application is vulnerable to HTML and JavaScript injection attacks.
We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a local attacker to inject in JavaScript that will execute in the context of the FM Radio application, but the FM Radio has limited application permissions, but the injected HTML or JavaScript code could prevent a user from using the FM Radio application until a factory reset.
The vulnerability can be exploited locally by opening the FM Radio application, selecting a radio station, marking it as a favorite, and changing the station name to include HTML.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
After passing thru a number of hurdles, I put together a whitepaper documenting vulnerabilities that I found in the operating system and various security risks of the platform. The whitepaper was originally posted on the NCC Group research page (this is just another repost). There are a couple interesting bugs documented in the paper including details on how I chained together with an HTML injection vulnerability, a CSP bypass, and an over permission application in order to gain root-level access on one device.
“KaiOS is a mobile operating system, forked from the discontinued Firefox OS, in which all the mobile applications running on a KaiOS-based mobile device are built using web technologies, such as HTML, JavaScript, and CSS. In this independent research project, we demonstrate that six of the pre-installed mobile applications are vulnerable to remote and local, HTML injection attacks, which when combined with bypasses in the Content Security Policy can result in the abuse of privileged JavaScript APIs resulting in remote file disclosure or local privilege escalation. Additionally, we explore the security implications of both documented and undocumented JavaScript APIs in the platform and general security risks of the mobile platform.”
Exploring the Security of KaiOS Mobile Apps
The following vulnerabilities affected multiple KaiOS mobile devices:
Technical Advisories:
- KaiOS Email Application HTML Injection (CVE-2019-14756)Vendor: KaiOS Technologies Inc.
- Vendor URL: https://www.kaiostech.com/
- Versions affected: KaiOS 1.0, KaiOS 2.5, KaiOS 2.5.1.
- Systems Affected: KaiOS-based mobile devices
- CVE Identifier: CVE-2019-14756 Risk: High
Summary
KaiOS is a mobile operating system based on Firefox OS. The operating system comes with a number of pre-installed "certified" applications including the Email application, which allows a user to view their emails on the mobile device. Firefox OS mobile applications are built using JavaScript and HTML.The Email application is vulnerable to HTML and JavaScript injection attacks.
Location
/system/b2g/webapps/email.gaiamobile.org
Impact
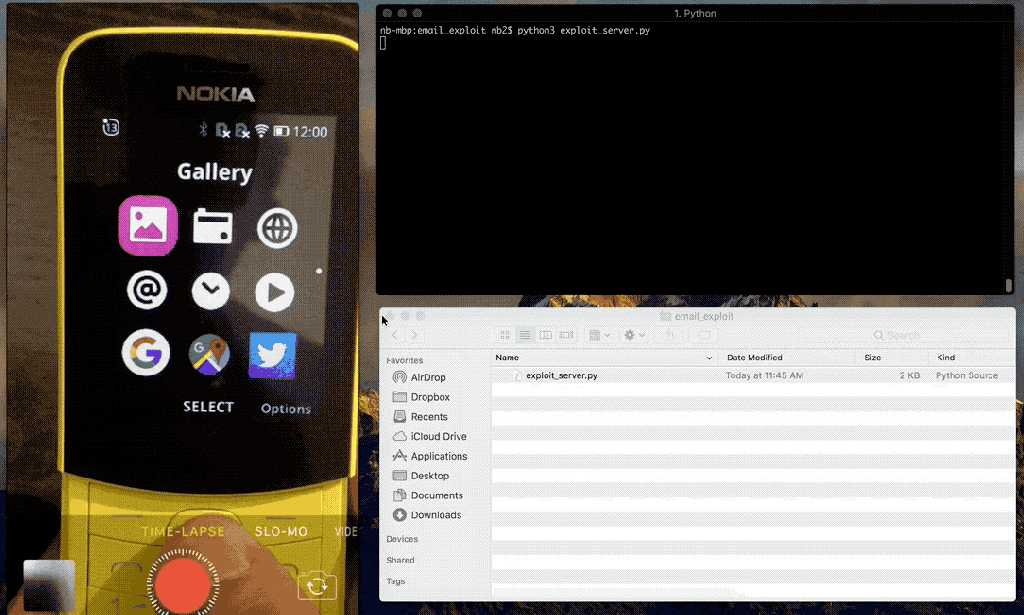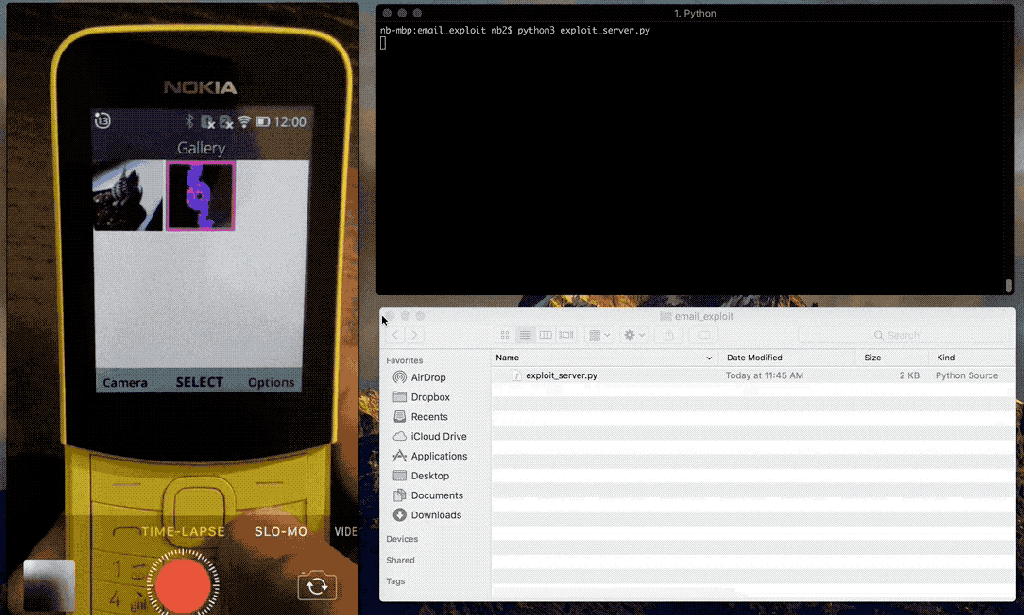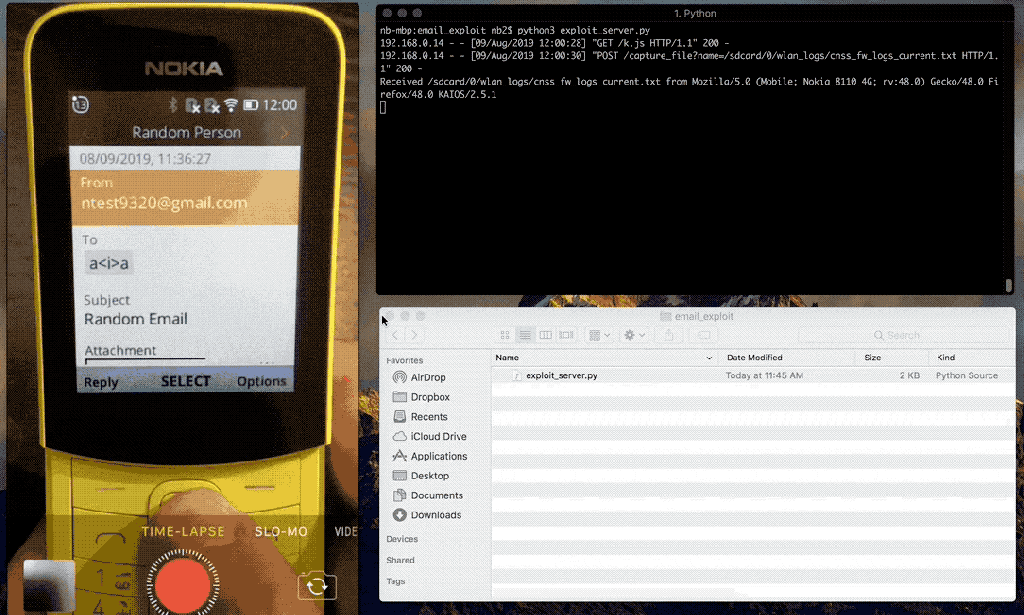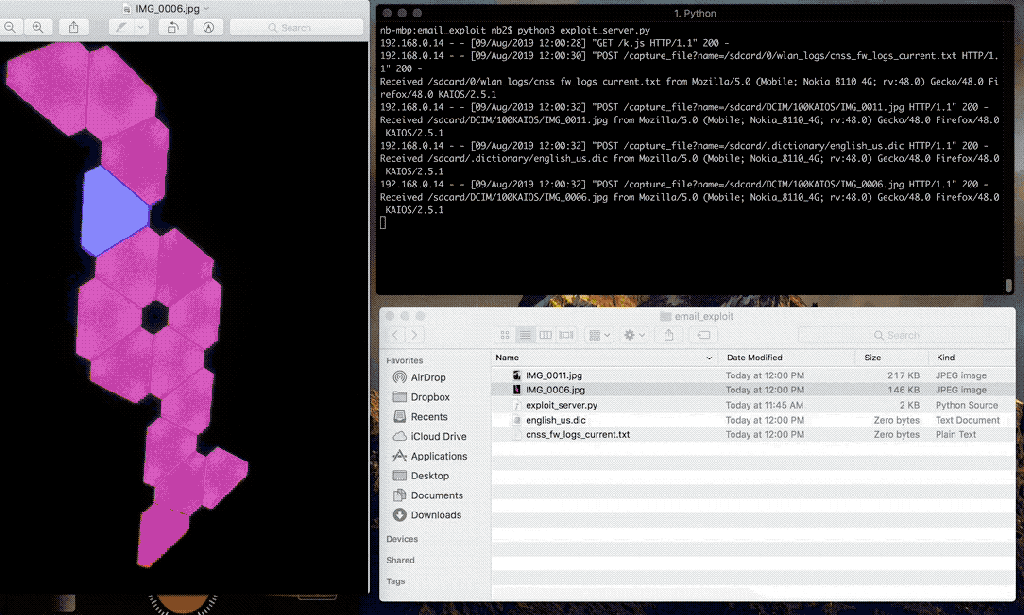
An attacker can send a specially crafted email to the victim which will inject HTML into the email application's UI as soon as the email is opened. At a bare minimum, this allows an attacker to take control over the Email application's UI and display a malicious prompt to the user asking them to re-enter their email credentials.We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a remote attacker to inject in JavaScript that will execute in the context of the Email application, which has access to sensitive Web APIs, such as the storage, settings, and contacts Web APIs, which would allow a remote attacker to steal files stored on the SD card, such as the user's photos, videos, or audio, and alter device settings.
Details
The Email application is vulnerable to HTML injection when rendering an email with an attachment filename that contains HTML content.Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
The following video demonstrates that remote exploitation resulting in remote file disclosure is possible.

Recommendation
Avoid using HTML/JavaScript injection sinks such as the innerHTML property and use the innerText property instead of or manually performing HTML output encoding or input validation on user inputs to mobile applications.- KaiOS Contacts Application HTML Injection (CVE-2019-14757)
- Vendor: KaiOS Technologies Inc.
- Vendor URL: https://www.kaiostech.com/
- Versions affected: KaiOS 2.5, KaiOS 2.5.1
- Systems Affected: KaiOS-based Mobile Devices
- CVE Identifier: CVE-2019-14757 Risk: Medium
Summary
KaiOS is a mobile operating system based on Firefox OS. The operating system comes with a number of pre-installed "certified" applications including the Contacts application, which allows a user to view and edit a list of contacts on the mobile device. Firefox OS mobile applications are built using JavaScript and HTML.The Contacts application is vulnerable to HTML and JavaScript injection attacks.
Location
/system/b2g/webapps/contact.gaiamobile.org
Impact
An attacker can send a vCard file to the victim which will inject HTML into the Contacts application assuming the victim chooses to import the file. At a bare minimum, this allows an attacker to take control over the Contacts application's UI and display a malicious prompt to the user asking them to re-enter credentials such as their KaiOS credentials to continue using the application.It is also possible to bypass the default CSP used by certified applications, which allows a remote attacker to inject in JavaScript that will execute in the context of the Contacts application, which has access to sensitive Web APIs, such as the storage, settings, and contacts Web APIs, which would allow a remote attacker to steal files stored on the SD card, such as the user's photos, videos, or audio, and alter device settings.
Details
The Contacts application is vulnerable to HTML injection when rendering a contact that contains HTML in its first or last name.The vulnerability could be exploited remotely if an attacker creates a vCard file using the first or last name that includes HTML content. The attacker then sends the vCard file as an email attachment to an email account that is set up on the mobile device. When the user selects the attachment from within the Email mobile application, then the Contacts application will open. If the user agrees to save the contact and then reopen the Contacts application then HTML injection will occur.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
Recommendation
Avoid using HTML/JavaScript injection sinks such as the innerHTML property and use the innerText property instead of or manually performing HTML output encoding or input validation on user inputs to mobile applications.- KaiOS File Manager Application HTML Injection (CVE-2019-14758)
- Vendor: KaiOS Technologies Inc.
- Vendor URL: https://www.kaiostech.com/
- Versions affected: KaiOS 2.5, KaiOS 2.5.1
- Systems Affected: KaiOS-based Mobile Devices
- CVE Identifier: CVE-2019-14758 Risk: Medium
Summary
KaiOS is a mobile operating system based on Firefox OS. The operating system comes with a number of pre-installed "certified" applications including the File Manager application, which allows the user to view and delete files on the device's internal storage or external storage. Firefox OS mobile applications are built using JavaScript and HTML.The File Manager application is vulnerable to HTML and JavaScript injection attacks.
Location
/system/b2g/webapps/filemanager.gaiamobile.org
Impact
An attacker can send a file via email to the victim which will inject in HTML into the File Manager application assuming the victim chooses to download the email attachment and view the downloads directory via the File Manager. Note that the KaiOS browser sanitizes filenames of files downloaded from the Internet, but other third-party KaiOS mobile applications could also download files over the Internet with malicious filenames that would trigger this vulnerability. Alternatively, a file, with a malicious filename, could be transferred via USB to a mobile device if attached to a hostile computer. At a bare minimum, this allows an attacker to take control over the File Manager application's UI and display a malicious prompt to the user asking them to re-enter credentials such as their KaiOS credentials to continue using the application.We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a remote attacker to inject in JavaScript that will execute in the context of the File Manager application, which has access to sensitive Web APIs, such as the storage Web APIs, which would allow a remote attacker to steal files stored on the SD card, such as the user's photos, videos, or audio. On mobile devices where the File Manager has been granted access to an undocumented engineering mode Web API, it is possible to execute arbitrary OS commands as the root user by exploiting this vulnerability.
Details
The File Manager application is vulnerable to HTML injection when rendering a filename that contains HTML.The vulnerability can be exploited locally by connecting the mobile device to a computer using USB and transferring the malicious file to the mobile device's internal storage using MTP. Opening the File Manager application and viewing the malicious filename triggers HTML injection into the mobile application.
The vulnerability can be exploited remotely by sending the file as an email attachment to an email account that is set up on a mobile device. If the user downloads the file attachment and then accesses the downloads directory via the File Manager application.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
Recommendation
Avoid using HTML/JavaScript injection sinks such as the innerHTML property and use the innerText property instead of or manually performing HTML output encoding or input validation on user inputs to mobile applications.- KaiOS Recorder Application HTML Injection (CVE-2019-14760)
- Vendor: KaiOS Technologies Inc.
- Vendor URL: https://www.kaiostech.com/
- Versions affected: KaiOS 2.5
- Systems Affected: KaiOS-based mobile devices
- CVE Identifier: CVE-2019-14760 Risk: Low
Summary
KaiOS is a mobile operating system based on Firefox OS. The operating system comes with a number of pre-installed "certified" applications including the Recorder application, which allows the user to record and listen to audio. Firefox OS mobile applications are built using JavaScript and HTML.The Recorder application is vulnerable to HTML and JavaScript injection attacks.
Location
/system/b2g/webapps/soundrecorder.gaiamobile.org
Impact
A local attacker can inject arbitrary HTML into the Recorder application. At a bare minimum, this allows an attacker to take control over the Recorder application's UI and display a malicious prompt to the user asking them to re-enter credentials such as their KaiOS credentials to continue using the application.It is also possible to bypass the default CSP used by certified applications, which allows a local attacker to inject in JavaScript that will execute in the context of the Recorder application, which has access to sensitive Web APIs, such as the storage and settings Web APIs, which would allow a local attacker to manipulate files stored on the SD card, such as the user's photos, videos, or audio, and alter device settings.
Details
The Recorder application is vulnerable to HTML injection when rendering the name of a recording.The vulnerability can be exploited locally by opening the Recorder application and creating a new audio recording with a name that contains HTML.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
Recommendation
Avoid using HTML/JavaScript injection sinks such as the innerHTML property and use the innerText property instead of or manually performing HTML output encoding or input validation on user inputs to mobile applications.- KaiOS Note Application HTML Injection (CVE-2019-14761)
- Vendor: KaiOS Technologies Inc.
- Vendor URL: https://www.kaiostech.com/
- Versions affected: KaiOS 2.5
- Systems Affected: KaiOS-based mobile devices
- CVE Identifier: CVE-2019-14761 Risk: Low
Summary
KaiOS is a mobile operating system based on Firefox OS. The operating system comes with a number of pre-installed "certified" applications including the Note application, which allows the user to record simple text notes. Firefox OS mobile applications are built using JavaScript and HTML.The Note application is vulnerable to HTML and JavaScript injection attacks.
Location
/system/b2g/webapps/notes.gaiamobile.org
Impact
A local attacker can inject arbitrary HTML into the Note application. At a bare minimum, this allows an attacker to take control over the Note application's UI and display a malicious prompt to the user asking them to re-enter credentials such as their KaiOS credentials to continue using the application.We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a local attacker to inject in JavaScript that will execute in the context of the Note application, which has access to sensitive Web APIs, such as the storage Web APIs, which would allow a local attacker to manipulate files stored on the SD card, such as the user's photos, videos, or audio.
Details
The Note application is vulnerable to HTML injection when rendering the contents of the note on the main application screen.The vulnerability can be exploited locally by opening the Note application and creating a new note with contents that contain HTML.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
Recommendation
Avoid using HTML/JavaScript injection sinks such as the innerHTML property and use the innerText property instead of or manually performing HTML output encoding or input validation on user inputs to mobile applications.- KaiOS FM Radio HTML Injection (CVE-2019-14759)
- Vendor: KaiOS Technologies Inc.
- Vendor URL: https://www.kaiostech.com/
- Versions affected: KaiOS 1.0, KaiOS 2.5, KaiOS 2.5.1
- Systems Affected: KaiOS-based mobile devices
- CVE Identifier: CVE-2019-14759 Risk: Low
Summary
KaiOS is a mobile operating system based on Firefox OS. The operating system comes with a number of pre-installed "certified" applications including the FM Radio application, which allows the user to listen to the radio. Firefox OS mobile applications are built using JavaScript and HTML.The FM Radio application is vulnerable to HTML and JavaScript injection attacks.
Location
/system/b2g/webapps/fm.gaiamobile.org
Impact
A local attacker can inject arbitrary HTML into the FM Radio application. At a bare minimum, this allows an attacker to take control over the FM Radio application's UI and display a malicious prompt to the user asking them to re-enter credentials such as their KaiOS credentials to continue using the application.We have also demonstrated that it is possible to bypass the default CSP used by certified applications, which allows a local attacker to inject in JavaScript that will execute in the context of the FM Radio application, but the FM Radio has limited application permissions, but the injected HTML or JavaScript code could prevent a user from using the FM Radio application until a factory reset.
Details
The FM Radio application is vulnerable to HTML injection when rendering the name of a favorite radio station on the main application screen.The vulnerability can be exploited locally by opening the FM Radio application, selecting a radio station, marking it as a favorite, and changing the station name to include HTML.
Privileged and certified mobile applications use a default Content Security Policy to prevent JavaScript injection, but we have noted that we are able to bypass the CSP by injecting in an iframe using the srcdoc attribute, which is a publicly documented technique.
Recommendation
Avoid using HTML/JavaScript injection sinks such as the innerHTML property and use the innerText property instead of or manually performing HTML output encoding or input validation on user inputs to mobile applications.After passing thru a number of hurdles, I put together a whitepaper documenting vulnerabilities that I found in the operating system and various security risks of the platform. The whitepaper was originally posted on the NCC Group research page (this is just another repost). There are a couple interesting bugs documented in the paper including details on how I chained together with an HTML injection vulnerability, a CSP bypass, and an over permission application in order to gain root-level access on one device.
“KaiOS is a mobile operating system, forked from the discontinued Firefox OS, in which all the mobile applications running on a KaiOS-based mobile device are built using web technologies, such as HTML, JavaScript, and CSS. In this independent research project, we demonstrate that six of the pre-installed mobile applications are vulnerable to remote and local, HTML injection attacks, which when combined with bypasses in the Content Security Policy can result in the abuse of privileged JavaScript APIs resulting in remote file disclosure or local privilege escalation. Additionally, we explore the security implications of both documented and undocumented JavaScript APIs in the platform and general security risks of the mobile platform.”
Exploring the Security of KaiOS Mobile Apps
Post a Comment