What is DevSecOps : What Tools for DevSecOps
What is DevSecOps?
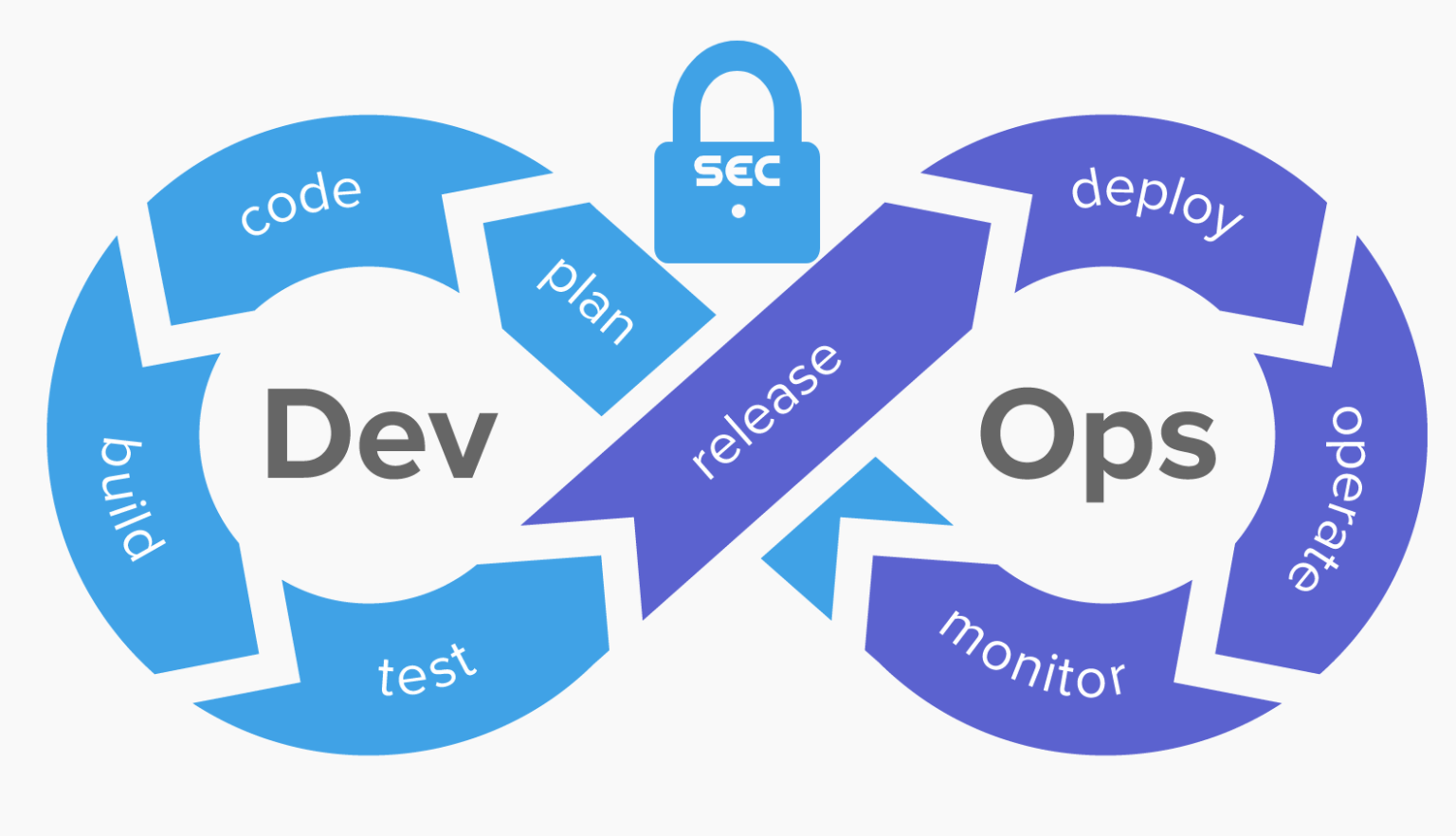
DevSecOps is security as a code culture where you integrate security tools in the DevOps lifecycle. Security as a part of the DevOps process is the only way to mitigate the risks.It is a transformational shift that incorporates security culture, practices, and tools in each phase of the DevOps processes. It removes the silos between the development, security, and operations teams.
It follows the shift-left approach, which means injecting security processes early into the design/plan stage to provide security awareness to development and operations teams and fulfill the cybersecurity requirements. The recent rise in high profile ransomware attacks has driven DevSecOps into top priority for DevOps teams. Encouraging a ‘Security as Code’ mindset within a team creates best practices right from the start of a project.
These are the practices of how DevSecOps is being implemented:
- Collaborating with security and development teams on the threat model.
- Integrating security tools in the development integration pipeline.
- Prioritizing the security requirements as a part of the product backlog.
- Reviewing infrastructure-related security policies before deployment.
- Security experts are evaluating automated tests.
Tools
It requires many technology stacks with several solutions that need to be carefully integrated to deploy the DevSecOps culture without creating gaps or creating bottlenecks in security.Below are some important and trending DevSecOps tools:
SonarQube: used for continuous inspection for code quality. It provides continuous feedback on software quality.
ThreatModeler: provides a threat modeling solution that scales and secures the enterprise software development lifecycle. It predicts, identifies, defines security threats, and helps you in saving time and cost.
Aqua Security: provides prevention, detection, and response automation to secure the build, secure cloud infrastructure, and secure running workloads. It secures the entire application lifecycle.
CheckMarx: a complete suite of software security solutions. This suite provides security testing for static and dynamic applications, tools like software composition analysis, and code bashing to promote software security culture among developers.
Fortify: provides application security as a service. It is used majorly in enterprises for Secure development, security testing, and continuous monitoring and protection.
HashiCorp Vault: manage secrets like passwords, tokens, API keys, certificates, and protect such sensitive data. There is more secret manager you can explore here.
GauntLT: a behavior-driven development tool to automate attack tools. It can easily integrate with your organization’s testing tools and processes.
IriusRisk: provides production-level application security at scale. It helps you manage threat models and security risks using two-way synchronization with testing tools and issue trackers with a real-time security activity view.
DevSecOps Ecosystem
This is the flow of different phases in the DevSecOps ecosystem. Here security scanning will be a part of the complete ecosystem.- In the development phase, security tools and plugins can be integrated into the IDE environment directly, identifying any source code vulnerability.
- You can integrate pre-commit hooks that will not allow committing any insecure data content like authentications keys to the repository and keep such data on the developer’s machine only.
- Version control will maintain secret management and configurations at the repository level.
- Pre and post-build will ensure static and dynamic code reviews, execution, and feedback.
- QA environment will check for security scanning and especially third-party component scanning.
- While the staging environment will execute vulnerability and penetration testing, the results will be shared with development, quality, and security teams.
- Automated security scanning on the production environment for Infrastructure as a code, Compliance as a code, and Security as a code will mitigate many manual security activities.
- Finally, monitoring the environment will enable alerts and notifications for security thresholds.
- Vulnerability management will be a part of the entire DevSecOps ecosystem.
CI/CD Process Security
- Integrate security scanners for containers: This should be part of the process for adding containers to the registry.
- Automate security testing in the CI process: This includes running security static analysis tools as part of builds, as well as scanning any pre-built container images for known security vulnerabilities as they are pulled into the build pipeline.
- Add automated tests for security capabilities into the acceptance test process: Automate input validation tests, as well as verification authentication and authorization features.
- Automate security updates, such as patches for known vulnerabilities: Do this via the DevOps pipeline. It should eliminate the need for admins to log into production systems while creating a documented and traceable changelog.
- Automate system and service configuration management capabilities: This allows for compliance with security policies and the elimination of manual errors. Audit and remediation should be automated as well.


Post a Comment